Nessus is a powerful network security scanner which will audit a given host or network and determine if any detected network services are vulneraable or can be misused by an intruder. This tool is much more than a network port scanner, it test for numerous current exploits, and it identifies and test services running on nonstandard ports. Nessus is built using a client/server architecture allowing an entire network segment to be tested and analyzed at once.
An external plug-in architecture is used for each security test plugin. As new tests are developed, they can be added without upgrading the core nessus client/server application. The security plugins are developed in a native nessus language called: NASL (Nessus Attack Scripting Language).
There are a number of ways for the NST user to work with nessus. The command line interface is used to launch the nessusd server daemon. Control of the nessus server can be through the command line or the X Windows interface. Getting fancier, one can also use a Secure Virtual Computing tunnel (Chapter 8, Virtual Computing) to perform a nessus scan remotely. Scan results produced by nessus can be stored in HTML format. Access to these results can be accomplished using the firefox web browser or the Apache web server running on NST.
NST is configured with a startup script for running the nessus application. The first form of the script: /usr/local/sbin/start_nessusd creates a nessus runtime environment along with setting up a file directory structure for the external nessus security test plugins. The nessusd daemon will also be started. The second form of this script can be used to terminate the nessusd daemon and optionally remove the external nessus security test plugins. The third form of this script is used to update the nessusd daemon "on-the-fly" with the latest external security plugins from the nessus web site.
NST's Web User Interface found in Chapter 2, The Web User Interface (WUI) can also be used to launch this script and run a default scan on a selected host, a number of hosts, or an entire network. Information on how to start nessus via NST's WUI can be found in the section called “Probing With Nessus”.
Note 1:
NST Memory Management Discussion With Nessus:
Nessus requires a significant amount of disk space (over 100MB) for operation with NST. Although one can get away with using only 256MB of RAM, we recommend a system having a minimum of 512MB. This is a definite recommendation if one wants nessus and the X nessus client.
The default RAM disk size is now set at 84MB using the default device:
/dev/ram4.The external security plugin updates require over 42MB of disk space. NST now uses the
/dev/shmShared Memory partition for download and installation.
Note 2:
Various System Configuration Suggestions For Using Nessus With NST:
Minimum system RAM: 512MB
Use a linux swap partition (see: auto_add_swap or alias: laddswap).
Use a hard disk partition for the external security plugins (use option: -rdir <runtime directory>).
Use the NST hard disk installation (see: nsthdinstall).
The following caption displays the documentation usage for the /usr/local/sbin/start_nessusd script:
[root@probe root]#/usr/local/sbin/start_nessusd -hUsage: start_nessusd [-u] [-rd <RAM device>] [-rds <RAM disk size (MB)>] [-rmp <RAM mount point>] [-rdir <runtime directory>] [-d] [-v] [-h] start_nessusd -s [-d [-rdir <runtime directory>]] [-v] start_nessusd -u [-v] The first form of this script is used to create a runtime execution environment for nessus and start the nessusd daemon. nessus is a powerful, up-to-date and easy to use remote security scanner. The default configuration will create a 84MB RAM disk for nessus and its associated external security plugins at directory location: "/mnt/ram4/nessus/plugins". The second form of this script is used to terminate a nessusd daemon and optionally remove the complete nessus runtime directory. The third form of this script is used to update nessus with the latest external security plugins from the nessus web site. Access to scanned results produced by nessus in HTML format can be made remotely available via the NST Apache Web Server or viewed locally by the firefox or elinks web browser. -u | --update-plugins First form: This parameter specifies whether or not to update nessus with the latest external security plugins from the nessus web site. This parameter is used with this form to initialize the nessusd server with access to the latest plugins that currently exist. Third form: One can update a nessusd server on-the-fly with this parameter. If new plugins are introduced, an already running nessusd process can be updated with the latest external security plugins by using this form. **Note: Internet access is required in order to update nessus with the latest plugins from the nessus web site. -s | --stop First form: Use this optional parameter to stop an already running nessusd daemon. If this option is not used and a nessusd daemon is already in progress, this script will terminate normally leaving the existing nessusd daemon running. Second form: This parameter is used stop a currently running nessusd daemon. The script will terminate once the nessusd daemon is stopped. -d | --delete First form: Use this optional parameter to delete a previous nessus runtime directory file structure (plugins) prior to starting up the nessusd daemon. Second form: Use this optional parameter to delete a previous nessus runtime directory file structure (plugins) when terminating a nessusd daemon. -rd <RAM device> | --ram-device <RAM device> Use this optional parameter to change the default RAM device that will be used for this instance of nessusd. The available RAM device names on NST are: "/dev/ram0 - /dev/ram9". A cooresponding mount point: "/mnt/ram0 - /mnt/ram9" will be automatically selected for the RAM device. One can use the following optional parameter: "-rmp <mount point>" to change mount point location for the selected RAM device. Default: "/dev/ram4" -rds <RAM dsk size (MB)> | --ram-disk-size <RAM disk size (MB)> Use this optional parameter to change the default RAM disk size in MegaBytes (MB) that will be used for nessus and the external security plugins. Default: "84" ** Note: Use a reasonable value and make sure you to not exceed your available system RAM. The system memory utility: "free" can be used to help make your determination. -rmp <mount point> | --ram-mount-point <mount point> Use this optional parameter to change the selected RAM device's: "-rd <RAM device>" mount point for nessus and the external security plugins. Default: "/mnt/ram4" -rdir <runtime directory> | --runtime-directory <runtime directory> First Form: One can use this optional parameter to force the setup script to use an existing directory on a locally attached disk drive or a mounted network file system and bypass the creation of a RAM disk. To do this, make sure the directory initially exists prior to running this script. Example: Mount Point: "/dev/hda1" mount at: "/probe1" type ext3 (rw) Directory: "/probe1/nessus_scan_data" Use: "-rdir /probe1/nessus_scan_data" to create the top level runtime directory structure for nessus and the external security plugins. Directory Structure: nessus => /probe1/nessus_scan_data/nessus plugins => /probe1/nessus_scan_data/nessus/plugins Second form: Use this optional parameter with the delete nessus file directory structure option (-d or --delete) for the location of the nessus runtime directory to remove when terminating a nessesd daemon. -v | --verbose This optional switch will enable verbose output. Without this switch set, minimal output from the execution of this script will be displayed. -h | --help Displays this help information.
One uses the external security plugins that come with the NST distribution and optionally download the latest plugins from the Nessus web site. Internet access will be required to obtain the remote external security plugins.
Lets show an example of starting up a nessusd server daemon, download the latest external security plugins, create a default 84 MByte RAM disk using device: /dev/ram4, and enable verbose mode during script execution.
[root@probe root]#/usr/local/sbin/start_nessusd -u -d -v*** Creating a 84MByte RAM disk at mount point: "/mnt/ram4"... /root/bin/create_ramdisk -s 84 -d /dev/ram4 -m /mnt/ram4 -v ============================================================ = Creating a 86016KB RAM disk at mount point: /mnt/ram4... = ============================================================ *** Zeroing out RAM device: "/dev/ram4"... /bin/dd if=/dev/zero of=/dev/ram4 bs=1k count=86016 86016+0 records in 86016+0 records out *** Creating a 86016KB Linux ext2 file system on RAM device: "/dev/ram4"... /sbin/mke2fs -vm 0 /dev/ram4 86016 mke2fs 1.35 (28-Feb-2004) Filesystem label= OS type: Linux Block size=1024 (log=0) Fragment size=1024 (log=0) 21560 inodes, 86016 blocks 0 blocks (0.00%) reserved for the super user First data block=1 11 block groups 8192 blocks per group, 8192 fragments per group 1960 inodes per group Superblock backups stored on blocks: 8193, 24577, 40961, 57345, 73729 Writing inode tables: done Writing superblocks and filesystem accounting information: done This filesystem will be automatically checked every 26 mounts or 180 days, whichever comes first. Use tune2fs -c or -i to override. *** Mounting RAM disk device: "/dev/ram4" at mount point: "/mnt/ram4"... /bin/mount -t ext2 /dev/ram4 /mnt/ram4 *** Show all current mounts... /bin/df -k Filesystem 1K-blocks Used Available Use% Mounted on /dev/ram1 63461 27341 36120 44% / none 253436 0 253436 0% /dev/shm /dev/hda 358192 358192 0 100% /mnt/cdrom /dev/ram4 83286 13 83273 1% /mnt/ram4 *** Successfully created a 86016KB RAM Disk: "/dev/ram4" at mount point: "/mnt/ram4"... Creating a nessus user: root... printf "root\npass\n********\n********\ndefault accept\n" | /usr/local/sbin/nessus-adduser 2>&1 | /bin/grep 'user added.' Is that ok ? (y/n) [y] user added. *** Successfully added a nessus user: root... *** Extracting NST distribution nessus external security plugins to : /mnt/ram4/nessus/plugins... /bin/tar -C /mnt/ram4/nessus -xj -f /usr/local/lib/nessus/plugins/nessus_plugins.tar.bz2 *** Creating a new quick nessus SSL certificate... /usr/local/sbin/nessus-mkcert -q /usr/local/var/nessus/CA created /usr/local/com/nessus/CA created *** Successfully generated a quick nessus SSL certificate... *** Starting up nessusd... /usr/local/sbin/nessusd -D All plugins loaded nessusd successfully started... *** Getting latest nessus external security plugins from site: *** http://www.nessus.org/nasl/all-2.0.tar.gz /usr/local/sbin/nessus-update-plugins -v 04webserver.nasl 12planet_chat_server_path_disclosure.nasl 12planet_chat_server_plaintext_password.nasl 12planet_chat_server_xss.nasl . . . ssl_funcs.inc telnet_func.inc uddi.inc *** Successfully retrieved and updated nessus with the latest external security plugins...[root@probe root]#ps -ef | grep nessusdroot 1286 1 0 08:31 ? 00:00:00 nessusd: waiting for incoming connections[root@probe root]#
At this point one can now perform security scans using this NST host as a nessus server.
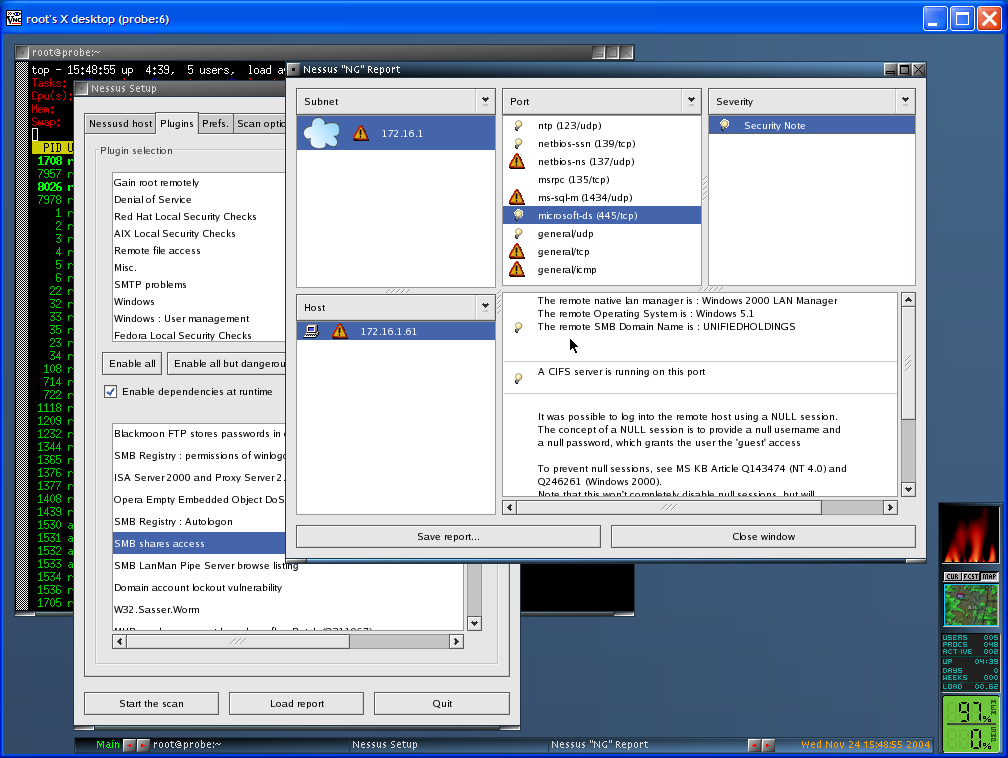
The screen shot below (Figure 3.7, “Nessus X Client (NST v1.2.1 and Above)”) shows the nessus X client rendered by a VNC client on a Windows XP desktop.
Note:
The NessusWX client for Win32 can also be used to attach to a nessusd server daemon running on a NST probe for security scanning sessions.