Table of Contents
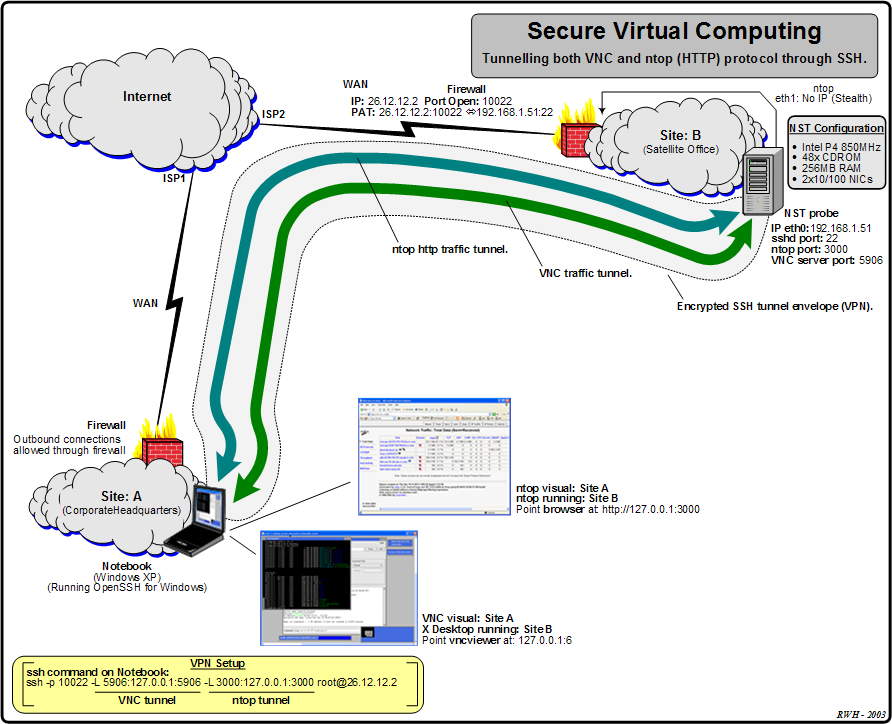
Secure Virtual Computing can be accomplish by tunnelling services or application protocols within an encrypted Secure Shell (ssh) session envelope. Figure 7.1, “Secure Virtual Computing” shows two applications; VNC and ntop that are tunnelled between a remote Satellite Office and the associated Corporate Headquarters through a ssh session.
This example also shows the use of Network and Port Address Translation (NAT) and (PAT) at the Satellite Office Firewall.